The number of people working from home has risen astronomically this year due to Covid-19. Consequently, numerous companies have been reliant on remote desktop connections to enable their employees to access their work computer from home.
One of the most popular applications for accessing Windows workstations and servers is Microsoft’s remote desktop protocol (RDP), which cyber criminals have viewed as the perfect opportunity to exploit.
To gain access to valuable corporate resources such as confidential emails and data, cyber criminals can deploy brute-force attacks, which attempt to find a valid RDP username and password pair by systematically checking all possible combinations until the right one is found.
Interested in the prevalence of RDP brute-force attacks, Reboot Online analysed the latest data from anti-virus specialists Kaspersky to discover which European countries are most at risk.
The Results:
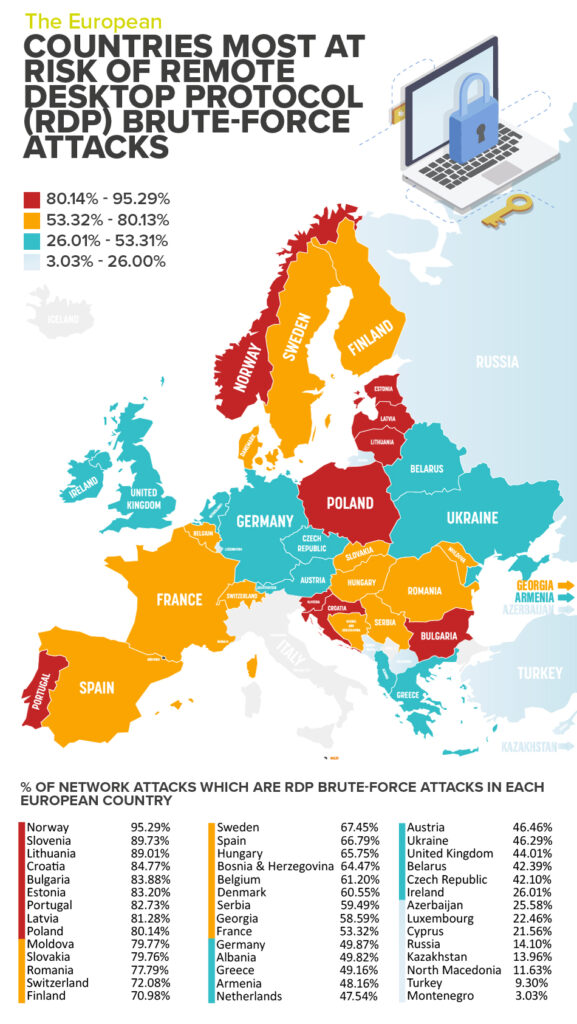
Reboot Online found that Norway is the biggest victim of RDP brute-force attacks in Europe, with majority of network attacks attributed to RDP brute-force attacks (95.29%).
Slovenia is in second position, as 89.73% of all network attacks in the country are RDP brute-force attacks leaving Microsoft users at high risk.
Slightly below Slovenia is Lithuania, 89.01% of their network attacks are RDP brute-force attacks, placing them as the third most likely to experience RDP brute-force attacks in Europe.
With the percentage of RDP brute-force attacks between 80%-85% other European countries at risk include: Croatia (84.77%), Bulgaria (83.88%), Estonia (83.20%), Portugal (82.73%), Latvia (81.28%) and Poland (80.14%).
The rate of RDP brute-force attacks in United Kingdom is 44.01%, meaning the country ranks 31st.
When it comes to the other major economic powerhouses of Europe, this is how they fare with the risk of RDP brute-force attacks: Switzerland (72.08%), Sweden (67.45%), Spain (66.79%), Belgium (61.20%), Denmark (60.55%), France (53.32%), Germany (49.87%) and Netherlands (47.54%).
Alternatively, North Macedonia (11.63%), Turkey (9.30%) and Montenegro (3.03%) are among the European countries where RDP brute-force attacks are significantly lower, placing them at the bottom of the list.
Reboot Online also provided top tips to help companies prevent RDP brute-force attacks
- Have strong usernames and passwords
A basic and easy form of defence against RDP brute-force attacks is having a strong password. A password which is long and contains a combination of upper-and-lower case letters, numbers and special characters is recommended.
Additionally, avoid basic account names such as ‘administrator’ as usernames, and instead use something more cryptic.
- Set remote access restrictions
Instead of granting access to RDP to everyone in the company, think about the employees or departments who truly need it to work. By restricting RDP access to selected personnel, you take a productive step towards reducing the risk of an attack.
- Account lockout policy
RDP brute-force attacks could require cyber criminals hundreds, thousands or even millions of login attempts before finding the correct credentials –slow potential attacks by setting up an account lockout policy on Microsoft Windows. This feature will lock a user if they fail to log-in after a certain number of times within a specified time frame.
- Assess IT estate
Carefully assess all the computers in your company and identify any outdated units that can be accessed from the internet using RDP. Once these computers have been identified, replace them as soon as possible. Outdated computers are unlikely to support any new security updates/patches thus making them more susceptible to cyber-attacks.
Read the latest edition of PCR’s monthly magazine below:
 PCR Tech and IT retail, distribution and vendor news
PCR Tech and IT retail, distribution and vendor news



